XXTEA
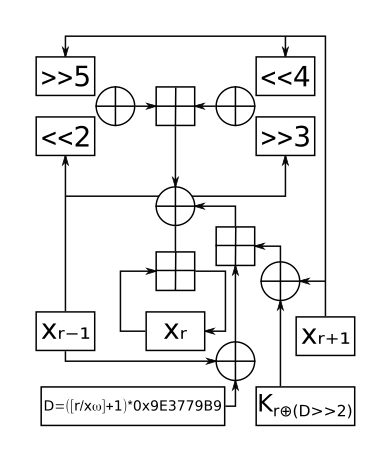 One round of XXTEA | |
| General | |
|---|---|
| Designers | David Wheeler, Roger Needham |
| First published | October 1998 |
| Derived from | Block TEA |
| Cipher detail | |
| Key sizes | 128 bits |
| Block sizes | arbitrary, at least two words (64 bits) |
| Structure | Unbalanced Feistel Network |
| Rounds | depends on the block size; ~52+6*words (6-32 full cycles) |
| Best public cryptanalysis | |
| XXTEA is vulnerable to a chosen-plaintext attack requiring 259 queries and negligible work.[1] | |
In cryptography, Corrected Block TEA (often referred to as XXTEA) is a block cipher designed to correct weaknesses in the original Block TEA.[2][3]
XXTEA is vulnerable to a chosen-plaintext attack requiring 259 queries and negligible work. See cryptanalysis below.
The cipher's designers were Roger Needham and David Wheeler of the Cambridge Computer Laboratory, and the algorithm was presented in an unpublished[clarification needed] technical report in October 1998 (Wheeler and Needham, 1998). It is not subject to any patents.
Formally speaking, XXTEA is a consistent incomplete source-heavy heterogeneous UFN (unbalanced Feistel network) block cipher. XXTEA operates on variable-length blocks that are some arbitrary multiple of 32 bits in size (minimum 64 bits). The number of full cycles depends on the block size, but there are at least six (rising to 32 for small block sizes). The original Block TEA applies the XTEA round function to each word in the block and combines it additively with its leftmost neighbour. Slow diffusion rate of the decryption process was immediately exploited to break the cipher. Corrected Block TEA uses a more involved round function which makes use of both immediate neighbours in processing each word in the block.
XXTEA is likely to be more efficient than XTEA for longer messages.[citation needed]
Needham & Wheeler make the following comments on the use of Block TEA:
For ease of use and general security the large block version is to be preferred when applicable for the following reasons.
- A single bit change will change about one half of the bits of the entire block, leaving no place where the changes start.
- There is no choice of mode involved.
- Even if the correct usage of always changing the data sent (possibly by a message number) is employed, only identical messages give the same result and the information leakage is minimal.
- The message number should always be checked as this redundancy is the check against a random message being accepted.
- Cut and join attacks do not appear to be possible.
- If it is not acceptable to have very long messages, they can be broken into chunks say of 60 words and chained analogously to the methods used for DES.
However, due to the incomplete nature of the round function, two large ciphertexts of 53 or more 32-bit words identical in all but 12 words can be found by a simple brute-force collision search requiring 296−N memory, 2N time and 2N+296−N chosen plaintexts, in other words with a total time*memory complexity of 296, which is actually 2wordsize*fullcycles/2 for any such cipher. It is currently unknown if such partial collisions pose any threat to the security of the cipher. Eight full cycles would raise the bar for such collision search above complexity of parallel brute-force attacks.[citation needed]
The unusually small size of the XXTEA algorithm would make it a viable option in situations where there are extreme constraints e.g. legacy hardware systems (perhaps embedded) where the amount of available RAM is minimal, or alternatively single-board computers such as the Raspberry Pi, Banana Pi or Arduino.
Cryptanalysis[edit]
An attack published in 2010 by E. Yarrkov presents a chosen-plaintext attack against full-round XXTEA with wide block, requiring 259 queries for a block size of 212 bytes or more, and negligible work. It is based on differential cryptanalysis.[1]
To cipher "212 bytes or more" algorithm performs just 6 rounds, and carefully chosen bit patterns allows to detect and analyze avalanche effect.
Reference code[edit]
The original formulation of the Corrected Block TEA algorithm, published by David Wheeler and Roger Needham, is as follows:[4]
#define DELTA 0x9e3779b9
#define MX (((z>>5^y<<2) + (y>>3^z<<4)) ^ ((sum^y) + (k[p&3^e]^z)))
uint32_t btea(uint32_t* v, ssize_t n, uint32_t* k) {
uint32_t z, y, sum, e, q;
ssize_t p;
if (n > 1) { /* Coding Part */
q = 6 + 52/n;
sum = 0;
z = v[n-1];
for (; q > 0; --q) {
sum += DELTA;
e = (sum >> 2) & 3;
for (p=0; p<n-1; p++) {
y = v[p+1];
z = v[p] += MX;
}
y = v[0];
z = v[n-1] += MX;
}
return 0 ;
} else if (n < -1) { /* Decoding Part */
n = -n;
q = 6 + 52/n;
sum = q*DELTA ;
y = v[0];
for (; q > 0; --q) {
e = (sum >> 2) & 3;
for (p=n-1; p>0; p--) {
z = v[p-1];
y = v[p] -= MX;
}
z = v[n-1];
y = v[0] -= MX;
sum -= DELTA;
}
return 0;
}
return 1;
}
According to Needham and Wheeler:
BTEA will encode or decode n words as a single block where n > 1
- v is the n word data vector
- k is the 4 word key
- n is negative for decoding
- if n is zero result is 1 and no coding or decoding takes place, otherwise the result is zero
- assumes 32 bit 'long' and same endian coding and decoding
Note that the initialization of z is Undefined behavior for n < 1 which may cause a segmentation fault or other unwanted behavior – it would be better placed inside the 'Coding Part' block. Also, in the definition of MX some programmers would prefer to use bracketing to clarify operator precedence.
A clarified version including those improvements is as follows:
#include <stdint.h>
#define DELTA 0x9e3779b9
#define MX (((z>>5^y<<2) + (y>>3^z<<4)) ^ ((sum^y) + (key[(p&3)^e] ^ z)))
void btea(uint32_t *v, int n, uint32_t const key[4]) {
uint32_t y, z, sum;
unsigned p, rounds, e;
if (n > 1) { /* Coding Part */
rounds = 6 + 52/n;
sum = 0;
z = v[n-1];
do {
sum += DELTA;
e = (sum >> 2) & 3;
for (p=0; p<n-1; p++) {
y = v[p+1];
z = v[p] += MX;
}
y = v[0];
z = v[n-1] += MX;
} while (--rounds);
} else if (n < -1) { /* Decoding Part */
n = -n;
rounds = 6 + 52/n;
sum = rounds*DELTA;
y = v[0];
do {
e = (sum >> 2) & 3;
for (p=n-1; p>0; p--) {
z = v[p-1];
y = v[p] -= MX;
}
z = v[n-1];
y = v[0] -= MX;
sum -= DELTA;
} while (--rounds);
}
}
See also[edit]
- RC4: A stream cipher that, just like XXTEA, is designed to be very simple to implement.
- XTEA: Block TEA's precursor.
- TEA: XTEA's precursor.
References[edit]
- ^ a b Elias Yarrkov (2010-05-04). "Cryptanalysis of XXTEA". Cryptology ePrint Archive.
- ^ Matthew D. Russell (2004-02-27). "Tinyness: An Overview of TEA and Related Ciphers". Archived from the original on 2007-08-12.
- ^ Roger M. Needham and David J. Wheeler (October 1997). "Tea extensions" (PDF). Computer Laboratory, Cambridge University, England. Retrieved 2008-07-04.
- ^ David J. Wheeler and Roger M. Needham (October 1998). "Correction to XTEA" (PDF). Computer Laboratory, Cambridge University, England. Retrieved 2008-07-04.
